February 25, 2025 Internet and virtual life
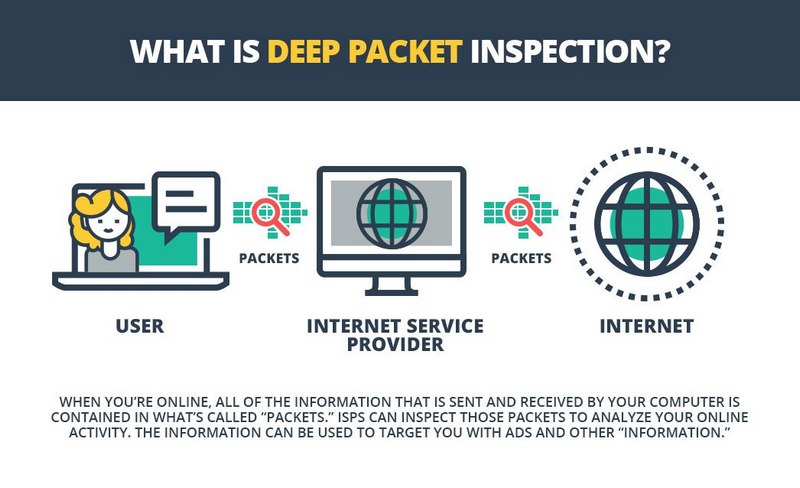
In the United States and the United Kingdom, Deep Packet Inspection is often used to generate advertisements based on subscriber behavior.
This is known as targeted marketing.
Deep Packet Inspection (DPI). It violates human rights, such as the right to privacy and the right to confidentiality
Deep Packet Inspection (DPI) is a technology that examines the content of network packets to regulate and filter traffic and collect statistical data.
Unlike firewalls, Deep Packet Inspection analyzes not only packet headers but also their content, starting at the second layer (data link) of the OSI model.
DPI technology enables ISPs and government agencies to apply flexible QoS policies to different types of traffic, restrict access to confidential resources, detect network intrusions, and stop the spread of computer viruses.
Deep Packet Inspection can make decisions based not only on packet content, but also on indirect signals inherent in certain network programs and protocols.
For this purpose, statistical analysis can be used (e.g. statistical analysis of the frequency of occurrence of certain symbols, packet length, etc.).
Sometimes Deep Packet Inspection of packets is used to block certain protocols, such as BitTorrent.
Deep Packet Inspection can help identify the application that generated or received the data and respond accordingly.
Detailed connection statistics can be collected for each user with Deep Packet Inspection.
In addition, QoS Deep Packet Inspection can control the transmission speed of individual packets, increasing or decreasing it as needed.
According to some ISPs, Deep Packet Inspection allows them to limit the applications that clog up the Internet channel by changing the transmission priorities of different types of data, such as speeding up the opening of Internet pages and reducing the download speed of large files.
Deep Packet Inspection is sometimes used in large companies to prevent accidental data loss and to protect internal files from being sent via email.
Firewall History
Early firewalls could be implemented in one of two ways.
In the first method, the proxy server protected the internal local network from outside access.
The proxy server verifies that network packets meet specified criteria.
It then filters or passes them on.
This method has traditionally been used to reduce the risk of someone exploiting protocol vulnerabilities.
The second method is to use a program that filters network packets according to a set of rules.
Such programs are called filtering firewalls.
A filtering firewall can block packets that do not match a few simple rules, such as source IP address, destination IP address, source port, and destination port.
These packet filters are the fastest firewalls available because they perform very few calculations.
The simplicity of implementation allows such a firewall to be implemented in the form of a microcircuit.
From the beginning, proxy servers were considered more secure than packet filters because they performed more detailed packet inspection.
The evolution of proxy-based firewalls led to the first deep packet inspection programs.
They were designed to solve network problems, block viruses, and protect against DoS attacks.
Initially, the computers on which deep packet inspection was installed were not powerful enough to monitor all users’ Internet traffic in real time.
After some time, when the ability to work in real time was introduced, Internet providers began to use Deep Packet Inspection programs mainly to deliver targeted advertisements and reduce network congestion.
Today, deep packet inspection can do much more than provide security.
ISPs have gained the ability to monitor the traffic of all their customers.
Having the tools to selectively block traffic gives ISPs the ability to offer additional services for a fee and generate additional revenue, even if it violates net neutrality.
Currently, in some countries, ISPs are required to perform filtering in accordance with local laws.
Deep Packet Inspection programs are sometimes used to detect and block traffic containing illegal or copyright-infringing material, or to gather information about websites visited for later sale to advertising networks.
Recently, the volume of traffic in transit has increased dramatically.
Again, the problem arises that computers cannot handle the analysis of all traffic in real time, or that the cost of computers is too high.
However, modern technologies already make it possible to create a fully functional deep packet inspection in the form of a special router.
Transport Layer Protocol Identification of the OSI Network Model
In the packet structure of the IPv4 protocol, a special byte is allocated to indicate the transport layer protocol number.
This is the tenth byte from the beginning of the IPv4 packet header.
For example, the number 6 indicates TCP and the number 17 indicates UDP ; using the tenth byte of the IPv4 protocol, it is possible to identify packets with TCP or UDP among all the packets transmitted.
There is also a special area in the IPv6 packet structure that contains a similar Transport Layer Protocol identifier.
This area is called the next header.
IP Identification
DPI devices can restrict access to hosts or resources based on their IP addresses.
This is a common, simple, inexpensive, and effective method of blocking prohibited content.
However, the IP address is not always the only unique identifier of the server.
In this case, allowed services hosted at the same IP address may also be affected.
This method is difficult to use effectively when using a content distribution network consisting of many variable IP addresses.
In Iran and China, access to proxy servers used to circumvent blocks, including those included in Tor, is restricted by IP address.
DNS Identification
One of the most common triggers for DPI is DNS requests.
In order to open a web page on the Internet, each user must send the domain name of the desired host or resource to the DNS server.
This packet exchange between the DNS server and the client takes place in unencrypted form using the UDP protocol.
A distinguishing feature of DNS that separates it from the rest of the traffic is that it operates exclusively on port 53.
As a result, DPI devices can detect requests addressed to any public DNS server.
Keywords
It is difficult to detect traffic for specific keywords because the payload is usually encrypted (the exception being exchanges over the http protocol).
The destination service can be indirectly determined from the server name indication string sent as part of the TLS session establishment in the unencrypted Client Hello message.
BitTorrent Identification
BitTorrent clients connect to the tracker using the TCP protocol.
To detect such packets among all TCP traffic, it is sufficient to verify that the data content of the TCP packet from the second byte matches the “BitTorrent protocol“.
In addition, to identify them, an analysis of the sequence of packets with the same characteristics, such as source_IP:port – destination_IP:port, packet size, frequency of opening new sessions per unit of time, etc., is performed according to behavioral models (heuristics) corresponding to such applications.
The interpretation of the behavioral models of the corresponding protocols, and therefore the accuracy of detection, varies from vendor to vendor.
HTTP Identification
To identify the HTTP protocol, simply verify that the packet is TCP and that the content of this TCP packet begins with one of the following commands: “GET”, “POST”, “HEAD”, “PUT”, “DELETE”, “CONNECT”, “OPTIONS”, “TRACE”, “PATCH”.
There should also be a space after the command, and after a while the text “HTTP/” should appear.
If all this is done, then the packet carries an HTTP request.
RTSP Identification
To detect RTSP packets in all traffic, just make sure that the packet is TCP and that the contents of this TCP packet starts with one of the following commands: “OPTIONS”, “DESCRIBE”, “ANNOUNCE”, “PLAY”, “SETUP”, “GET_PARAMETER”, “SET_PARAMETER”, “TEARDOWN”.
There must be a space after the command.
Also, the text “RTSP/” should appear after a while.
QoS Implementation
From an operational perspective, IPR at the application level allows the operator to control the utilization of the connected channels.
Traditionally, QoS (Quality of Service) has been implemented by solving problems exclusively through queuing based on marking traffic with service bits in IP, 802.1q and MPLS headers, where higher priority traffic (various types of VPNs, IPTV, SIP, etc.) is highlighted and guaranteed a certain transfer rate at any given time.
Best Effort traffic, which includes all HSI (High Speed Internet) traffic from home subscribers, was left virtually uncontrolled, allowing Bittorrent to consume all available bandwidth, resulting in the degradation of other web applications.
With IPR, the operator can divide the channel among different applications.
For example, at night, Bittorrent traffic can be made to use more bandwidth than during peak daytime hours when there is a lot of other web traffic on the network.
Another measure popular with many mobile operators is blocking Skype traffic and any type of SIP telephony.
Instead of complete blocking, the operator may allow these protocols to operate, but at very low speeds, with a corresponding degradation in the quality of service provided by a particular application, forcing the user to pay for traditional telephony services or for a special service package that allows access to VoIP services.
Software
Hippie (Hi-Performance Protocol Identification Engine) is an open source implementation of deep packet inspection for Linux written in C.
L7-filter is another open source implementation of Deep Packet Inspection for Linux written in C.
It focuses on classifying Layer 7 data from the OSI model.
SPID (Statistical Protocol IDentification) is another open source deep packet inspection implementation for Windows written in C#.
It identifies the OSI layer 7 protocol by statistical analysis of the traffic.
This technique allows data in packets to be modified.
In the United States and the United Kingdom, Deep Packet Inspection is often used to generate advertisements based on subscriber behavior.
This is called targeted marketing.
Major Russian mobile operators implemented DPI in 2009 (Megafon, Huawei), 2010 (MTS, Cisco) and 2011 (Beeline, Procera).
Among other things, they can use DPI to suppress peer-to-peer and VoIP services.
In contrast, Rostelecom pha introduced IPR for mobile Internet in 2014.
The Cypriot company iMarker (registered and operating under the laws of the Republic of Cyprus) has been offering ISPs free installation of IPR systems (Gigamon, Xterica) for targeted Internet advertising since the beginning of 2010.
Such a system receives information about all sites visited by users and can offer them personalized advertising.
According to Vedomosti, such a system has already been installed by 11 operators, including four regional branches of Rostelecom ; the company’s founder estimates that by the end of 2013 the total reach will be 12 percent of Russian Internet users.
Subsequently, iMarker became part of the American company Phorm, which offers similar services to European Internet providers.
In Russia, the trend of adoption of Deep Packet Inspection by ISPs is also connected with the Federal Law #139, which introduces amendments to the Law “On Protection of Children from Information Harmful to Their Health and Development” (which came into force on November 1, 2012).
Most ISPs block blacklisted sites based solely on the IP addresses of those sites.
However, some ISPs can block specific URLs if they use Deep Packet Inspection to analyze HTTP requests.
Applying DPI technology to encrypted connections (HTTPS) is difficult.
One of the obstacles to mandatory use of DPI technologies by Russian ISPs to block prohibited sites has been the high cost of such solutions, as well as the availability of cheaper alternatives for filtering by URL address for enforcement purposes.
Opponents of the use of Deep Packet Inspection argue that it violates human rights, such as the right to privacy and the right to confidentiality of correspondence, and that implementations do not comply with privacy regulations.
In addition, the use of Deep Packet Inspection to prioritize traffic violates net neutrality.
On May 12, 2017, in Azerbaijan, following the blocking of opposition news sites, all Internet calls were completely blocked (or limited to the maximum speed of access to the service), including messaging services such as Skype and WhatsApp.
At the same time, the government of the republic has not made any official statement on the matter.
As of September 27, 2020, due to the outbreak of the Second Karabakh War, the “Ministry of Transport, Communications and High Technologies of Azerbaijan” imposed restrictions on the use of the Internet in the country.
Facebook, WhatsApp, YouTube, Instagram, TikTok, LinkedIn, Twitter, Zoom and Skype platforms were completely blocked.
The block also affected VPN services, online banking services, and media sites.
P2P and UDP traffic has been actively suppressed since October 4, affecting Bittorrent and VoIP protocols.
Algorithms are used to identify and block IP addresses (incoming and outgoing traffic), which is why there are problems with instability of domestic servers abroad.
In 2018, the Belarusian government purchased DPI equipment from the American company Sandvine through the Russian supplier Jet Infosystems.
The equipment was used to block internet access on election day, August 9, 2020, and later after the protests began.